BSides Ft. Wayne 2022 Recap and CTF Writeup
Well, I suppose it’s better late than never, right? I meant to post this shortly after the conference but life has a habit of getting in the way sometimes! Back on May 21, I attended the inaugural BSides Fort Wayne information security conference. It was my first conference since Ohio Linuxfest 2018 and I had a great time! Sweetwater is an outstanding venue, and that’s not even mentioning their music and audio showroom, whose scale is astounding. I didn’t get to see all of the talks that I wanted to though, as the lockpicking village and CTF proved to be too much fun.
Of course I didn’t go alone, as I was joined by Trine Cybersecurity students and alumni. I think our program was represented quite well!
 Left to right: Eric Gaby, Jalan Albea, Thad Turner, Bryan Sears, Cameron Luzadder, Tanner Johnston.
Left to right: Eric Gaby, Jalan Albea, Thad Turner, Bryan Sears, Cameron Luzadder, Tanner Johnston.
CTF
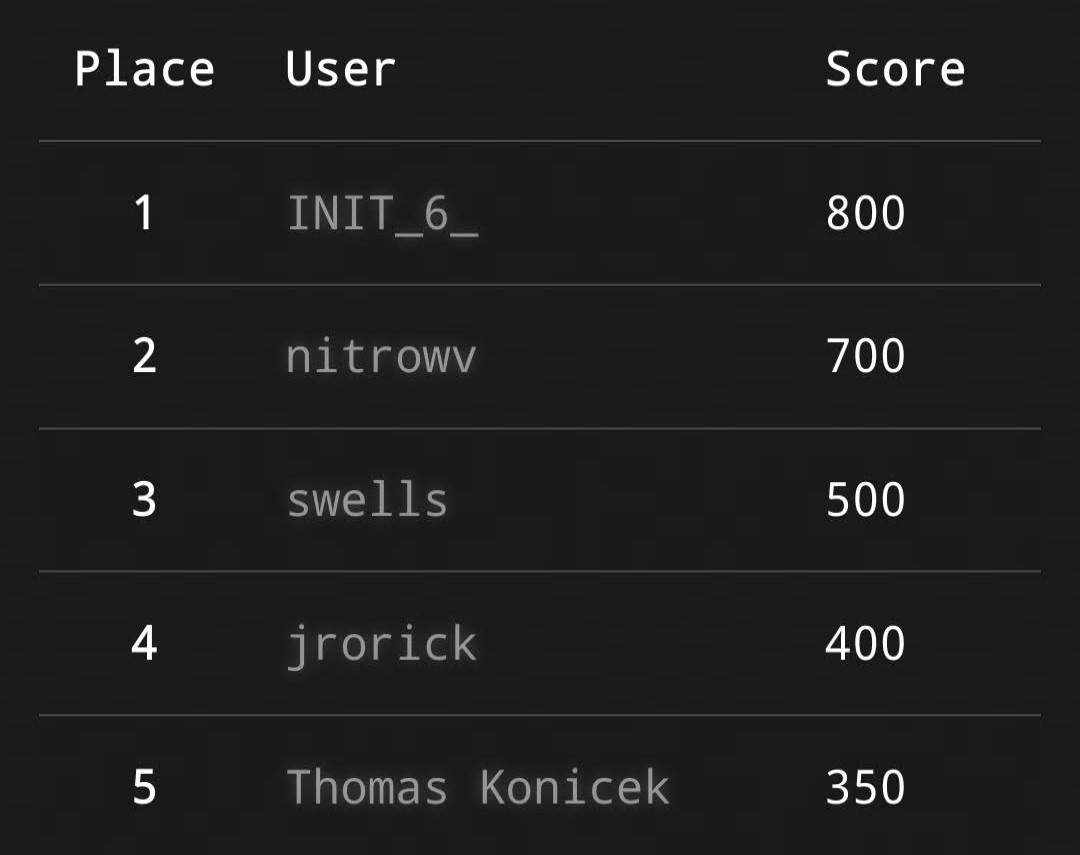
As for the CTF, I finished in 2nd place with 700 points, taking home a £100 HackTheBox gift card. It had a fun set of challenges that were designed with beginners and intermediates in mind.
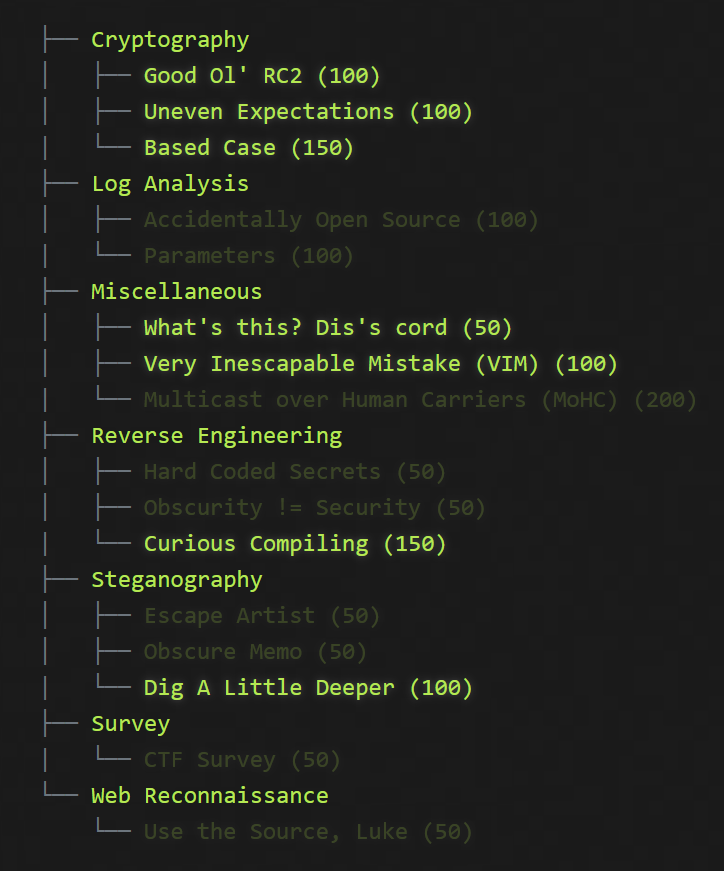
And here are said challenges. Unfortunately, I do not have the descriptions for any of these, which provide context and subtle hints about what to look for. I also lack the files for some of the challenges that I have completed, specifically Accidentally Open Source and Hard Coded Secrets. If anyone reading this has a copy of the original challenge files, please feel free to reach out!
With that being said, here are the writeups!
Log Analysis
Parameters
Points: 100
This challenge gives us an Apache log with HTTP requests:
1
2
3
**.***.***.** - lemke1570 [18/May/2022:20:05:45 -0400] "PUT /viral/markets HTTP/2.0" 416 12504
**.**.***.*** - - [18/May/2022:20:05:45 -0400] "PUT /partnerships/niches HTTP/2.0" 304 1348
***.***.**.** - - [18/May/2022:20:05:45 -0400] "POST /rich/bsftw{9X95ySYz0OYP9fbbrXiZkKEnUGawOGmV1Rop1L7mjhubY yJE6ZTapWDUCk5hLqhu8np7qOkb2Odq4 bR2S7kVJrHzA} HTTP/1.1" 205 6820
This challenge is similar to what we’ll see in Obscure Memo, but since this log has way more than three instances of the string bsftw, using regular expressions is more convenient than using cat and grep. All flags consist of bsftw{, 32 characters, and a }. While not the regex provided, we can use /bsftw{.{32}}/g to get us closer to what we’re looking for.
Using regexr.com to test, we see that there are two strings that match our regular expression:
1
2
bsftw{lSklv6GfDmjeDCWCm Hn1ju2fr3s mQ1}
bsftw{Regex_Is_The_Key_To_Text_Parsing}
That regular expression worked! We can see the correct flag of bsftw{Regex_Is_The_Key_To_Text_Parsing}.
Miscellaneous
Multicast over Human Carriers (MoHC)
Points: 200
This challenge was a nice change of pace, since in order to get the flag, we had to speak with the vendors that had a table at the event. I enjoy visiting the expo booths at conferences and learning more about the vendors and what they do. Each vendor had a fragment of the flag and we had to combine all ten of them into the correct flag. The fragments are as follows:
1
2
3
4
5
6
7
8
9
10
rkus
psbro
esno
asoc
twor
sesn
cial
lnet
otips
name
It took quite a while to fit the pieces together in the right order, but there were some parts that were easily decipherable. I was able to gather Asocialnetworkuses relatively quickly, but I was initially stumped on the order of the last bit, specifically over the placement of names and notips. Eventually, I got it in the right order and the correct flag is: bsftw{ASocialNetworkUsesNamesNotIpsBro}.
Reverse Engineering
Obscurity != Security
Points: 50
In this challenge, we are given a binary that, when executed, has the following output:
1
2
3
4
5
6
7
8
9
10
11
12
┌──(tanner㉿kali)-[~/ctf/bsides]
└─$ ./RE2
Hello BSIDES FW CTF Contestant!!
Can you find my secret?
****MENU****
1 - SysInfo
2 - Search - (WIP)
3 - (WIP)
4 - (WIP)
Please select Menu Number:
Selecting option 1 results in the following;
1
2
Please select Menu Number: 1
Why did you trust this application?!?!
Whereas selecting any of the other options shows the following:
1
2
Please select Menu Number: 2
Nothing to see Here... Yet
Before using tools such as Ghidra, I like to run the strings to see if there is any helpful information that hasn’t been obfuscated. When I ran strings on this binary, I did find some interesting strings listed:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
Hello BSIDES FW CTF Contestant!!
Can you find my secret?
****MENU****
1 - SysInfo
2 - Search - (WIP)
3 - (WIP)
4 - (WIP)
Please select Menu Number:
PLEASE INSERT A VALID OPTION.
YOU FOUND MY SECRET!!!
FFEjwtItjxStyJvzfqSzqqTwItjxNyFF
FLAG:
bsftw{
Why did you trust this application?!?!
Nothing to see Here... Yet
Where do you computers start counting?
Not here... look some where else
basic_string::_M_construct null not valid
;*3$"
We can see a flag prefix and a string above it which doesn’t really make sense. There is also a helpful hint in the form of “Where do you computers start counting?”. Since many programming languages start counting at 0 instead of 1, maybe we could try that as an input?
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(tanner㉿kali)-[~/ctf/bsides]
└─$ ./RE2
Hello BSIDES FW CTF Contestant!!
Can you find my secret?
****MENU****
1 - SysInfo
2 - Search - (WIP)
3 - (WIP)
4 - (WIP)
Please select Menu Number: 0
YOU FOUND MY SECRET!!!
FLAG:bsftw{AAZeroDoesNotEqualNullOrDoesItAA}
That did the trick! We find the flag of bsftw{AAZeroDoesNotEqualNullOrDoesItAA} by using an option that was not made clear to us by the program. Let it be known that obscurity does not in fact, equal security, as evidenced here.
An interesting thing that I noticed while writing this writeup is that the string we found earlier, FFEjwtItjxStyJvzfqSzqqTwItjxNyFF, bears a resemblance to the flag. The FF at the beginning and end of this string seems to match with the AA in the actual flag. Sure enough, running it through CyberChef reveals that when the string is rotated by 21 (or -5) characters, we get the flag.
Steganography
Escape Artist
Points: 50
We are given a jpg file, named BSides_Logo_STEGO_1.jpg. When we open it in an image viewer, we see that it is simply the conference’s logo:
My first instinct in stego challenges like this is to look in the EXIF data and see if there’s anything interesting in there, so let’s do that.
You can do this a number of ways, but two of the tools that I use are exiftool and ImageMagick, both of which are included in Kali. Exiftool is a command-line tool that outputs the EXIF data in your terminal, while ImageMagick is a GUI program that can be used to manipulate images further.
First, we’ll use exiftool. To do this, I use the command exiftool BSides_Logo_STEGO_1.jpg, which gives us the following output:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(tanner㉿kali)-[~/ctf/bsides]
└─$ exiftool BSides_Logo_STEGO_1.jpg
ExifTool Version Number : 12.41
File Name : BSides_Logo_STEGO_1.jpg
Directory : .
File Size : 101 KiB
File Modification Date/Time : 2022:05:21 10:57:49-04:00
File Access Date/Time : 2022:06:01 19:22:56-04:00
File Inode Change Date/Time : 2022:06:01 19:22:21-04:00
File Permissions : -rwxrwxrwx
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.02
Exif Byte Order : Big-endian (Motorola, MM)
X Resolution : 150
Y Resolution : 150
Resolution Unit : inches
Artist : bsftw{TheArtistWhoDesignedThisIsGreat!}
Y Cb Cr Positioning : Centered
Displayed Units X : inches
Displayed Units Y : inches
XMP Toolkit : Adobe XMP Core 7.1-c000 79.a8731b9, 2021/09/09-00:37:38
Format : image/jpeg
Title : BSides_Logo_FW
Metadata Date : 2021:12:30 08:22:23-05:00
Modify Date : 2021:12:30 13:22:31Z
Create Date : 2021:12:30 08:22:23-05:00
In the Artist attribute, we find our flag, which is bsftw{TheArtistWhoDesignedThisIsGreat!}.
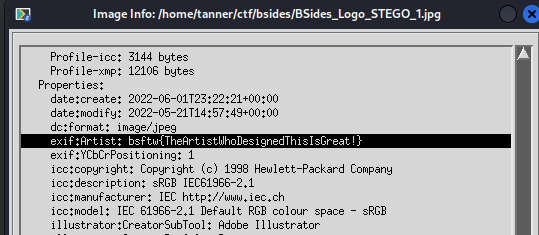
Doing this in ImageMagick is a similar process. After opening the image, click anywhere in the image window to bring up the command window. EXIF data is found by clicking Image Info in the Miscellany menu.
Scrolling down to the Properties section, we see our flag under the Artist attribute, just as we did using exiftool.
Obscure Memo
Points: 50
For this challenge, we are given two files; an image named web_logo.jpg and a text file named StegPasswords.txt, presumably containing passwords to extract data hidden in the image. The appearance of the image is the same as in the previous challenge, and the text file contains 101 possible passwords, with one on each line:
1
2
3
4
5
6
BSIDES
Wayne
security
Schedule
...
...
Since there are this many possible passwords, it isn’t feasible to try each of them manually. Fortunately, we can automate this process through scripting!
The actual extraction will be done using steghide, a program that allows for files to be embedded in and extracted from image and audio files.
To extract embedded content from a file, we need to specify what file has what we’re looking for (the stego file) and the password/passphrase. This is done using steghide extract -sf FILE.png -p PASSWORD.
As for automating this process, it is quite simple. All that’s needed is a for loop. My script and its output are fairly crude, but it gets the job done.
1
2
3
4
for i in $(cat StegPasswords.txt);
do echo 'Attempting passphrase: ' $i;
steghide extract -sf web_logo.jpg -p $i;
done
This script iterates through the password file and uses that line’s value in the steghide command.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(tanner㉿kali)-[~/ctf/bsides]
└─$ ./steghidebf.sh
Attempting passphrase: BSIDES
steghide: could not extract any data with that passphrase!
Attempting passphrase: Wayne
steghide: could not extract any data with that passphrase!
Attempting passphrase: security
steghide: could not extract any data with that passphrase!
Attempting passphrase: Schedule
steghide: could not extract any data with that passphrase!
...
...
Attempting passphrase: BSFTW
wrote extracted data to "BsidesCTF.txt".
...
The passphrase that was able to extract the data was BSFTW, and steghide wrote the data to a text file named BsidesCTF.txt, so let’s take a look at that.
1
2
3
4
5
Hello Bsides CTF Challeneger!
Are you enjoying Bsides FW? I hope you are! There is a flag some where in the text below! Will you find it?
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Aliquam malesuada bibendum arcu vitae elementum curabitur vitae nunc. Massa vitae tortor condimentum lacinia quis vel eros. Accumsan in nisl nisi scelerisque. Morbi quis commodo odio bsftw{This Is Not The Flag You Have Been Looking for!!} aenean sed adipiscing.
...
The text file contains lorem ipsum and at least one false flag. With the help of grep and Kali’s zsh syntax highlighting, I was able to better see the three occurrences of the flag prefix:
1
2
3
4
5
... Morbi quis commodo odio bsftw{This Is Not The Flag You Have Been Looking for!!} aenean sed adipiscing...
... Felis imperdiet bsftw{Maybe You Should read the requirements for a flag?} proin fermentum leo vel orci porta...
... Sagittis purus sit amet volutpat consequat bsftw{RegexIsCoolButIsVeryScaryAndHard} mauris nunc congue nisi. Senectus et netus et malesuada fames ac turpis egestas...
Looking at the flag format that we’ve seen so far, only the last fits the format, as it does not contain any spaces. It should be noted that the organizers did provide a regular expression of the flag format on the CTF scoreboard, which would have made this challenge a bit easier had I used it. Either way, we find that the flag is: bsftw{RegexIsCoolButIsVeryScaryAndHard}.
Web Reconnaissance
Use the Source, Luke
Points: 50
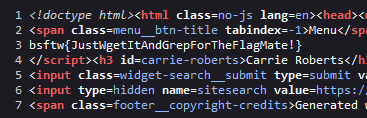
This challenge tells us that the flag is hidden in the source of one of the pages on the conference’s website. Since there are not that many pages on the website, I opted to use the view page source option in Firefox on every page, until finding the following on the Speakers page:
We find the correct flag of: bsftw{JustWgetItAndGrepForTheFlagMate!}. And yes, using wget and grep would have been a better way to do it!